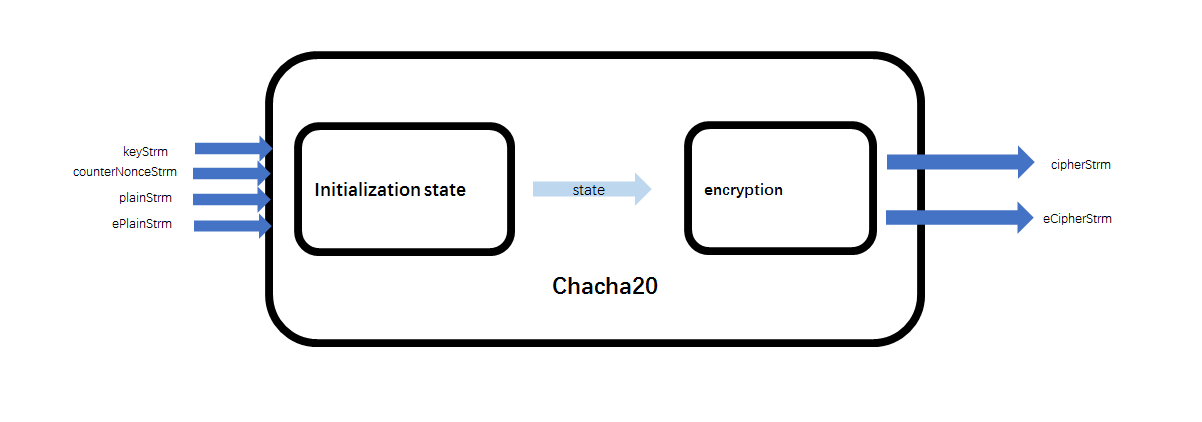
Chacha20 / Chacha20 Poly1305 Crypto Engine Ip Core
This is a legacy implementation. ChaCha20 is a stream cipher developed by Daniel J.

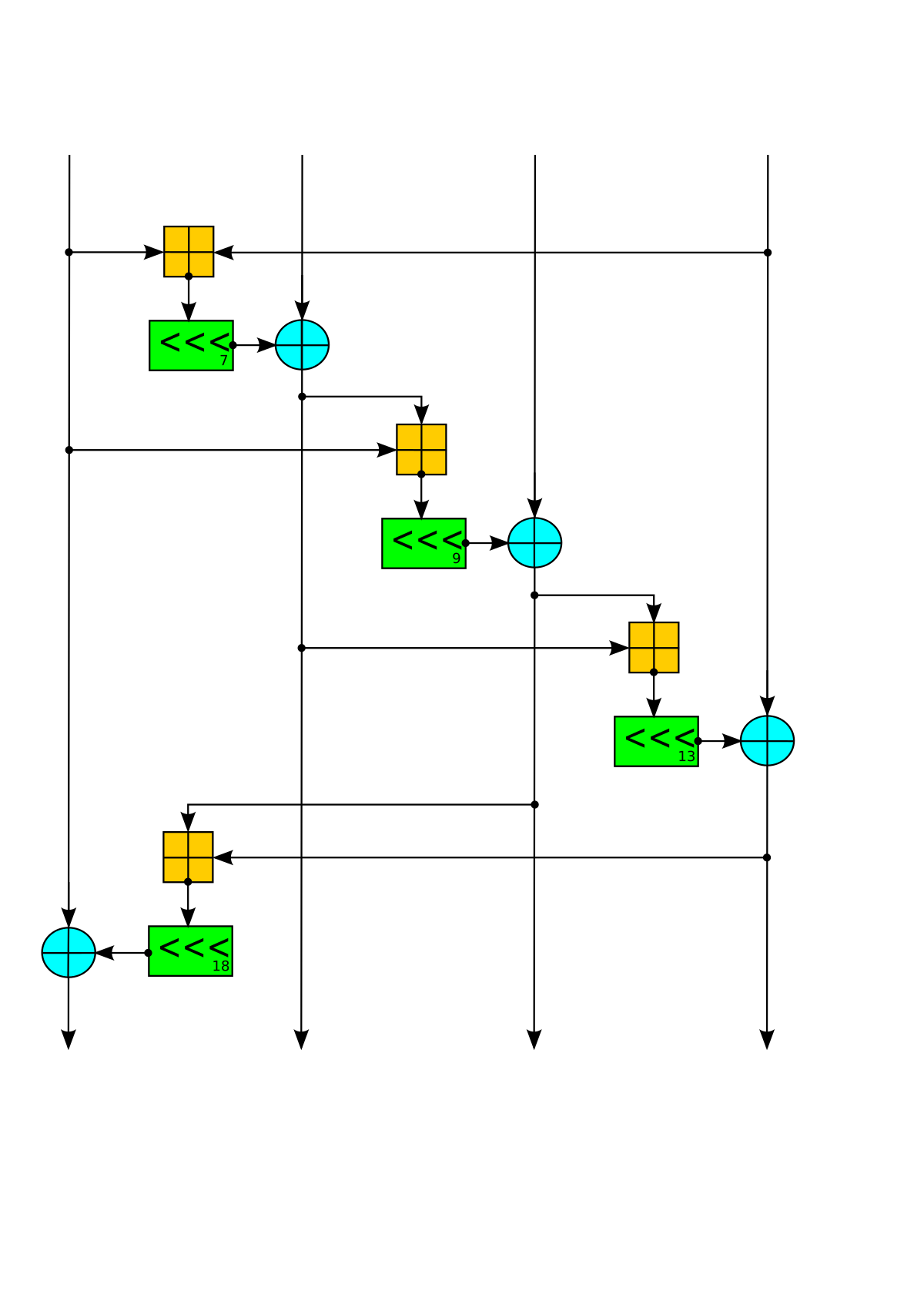
Chacha20 Algorithm Block Diagram Download Scientific Diagram
CentOS 7 配置 shadowsocks-libev 服务器端进行科学上网.
Chacha20. 高并发基于 libev 实现的异步 I. ChaCha12 and ChaCha20 are analogous modifications of the 12-round and 20-round ciphers Salsa2012 and Salsa2020. Cloudflare introduced the ChaCha20-Poly1305 cipher suite in February 2015 and immediately noticed performance benefits.
An AVXAVX2x64pure-Go implementation of the ChaCha20 stream cipher for Golang. Mbedtls_chacha20_setkey and mbedtls_chacha20_starts must be called at least once to setup the context before this function can be called. 2安装 vimgit 和 wget.
Shadowsocks-libev 是一个 shadowsocks 协议的轻量级实现是 shadowsocks-android shadowsocks-ios 以及 shadowsocks-openwrt 的上游项目. The x64 ChaCha20 implementations was taken from the public domain sources in SUPERCOP. So in a way and from the perspective of a programmer its not secure at all.
The bug appeared to be relatively rare when the cpu had AVX2 and it did not appear in other implementations like SSE or NEON. Poly1305 was published in 2004. The Salsa20 directory in version 20080120 of the eSTREAM benchmarking suite includes several implementations of ChaCha8 and ChaCha12 and ChaCha20.
A Cipher implements the cipherStream interface. Cipher is a stateful instance of ChaCha20 or XChaCha20 using a particular key and nonce. Nov 1 2016.
Yum install vim git wget -y. ChaCha20 is also not sensitive to timing attacks see the security considerations in Section 4. The AVX and AVX2 ChaCha20 implementations were taken from cloudflaresslconfig.
This paper presents the ChaCha family and explains the differences between Salsa20 and ChaCha. On occasion the tail of the cipher text would be incorrect. This algorithm is described in Section 24 2.
Its dangerous to use something so low-level. This is a high-speed message authentication code. ChaCha20 has a considerably bigger safety margin.
Chacha works great in general purpose CPUs and takes advantage of SIMD which exists on virtually all non-embedded CPUs and is hard to fuck up. 1 Introduction 11 Background The Salsa2020 stream cipher expands a 256-bit key into 264 randomly accessible. Internally XChaCha20 works like a block cipher used in counter mode.
ChaCha20 doesnt require any lookup tables and avoids the possibility of timing attacks. Implementation is also straightforward and easy to get right. For example in Too Much Crypto the authors recommend 11 instead of 14 for AES-256 and 8 rounds instead of 20 for ChaCha as safe.
Find out how to manage your cookies at AllAboutCookiescouk Our site is a participant in the Amazon EU Associates Programme an affiliate advertising programme. Also see Issue 1069 and Commit 20962baf4440. It is a variant of Salsa20 with better diffusion.
This is a cipher vulnerability not limited to any specific SSLTLS software implementation. XChaCha20 is a variant of ChaCha20 with an extended nonce allowing random nonces to be safe. 完成后执行 git version 如果出版本号则安装成功.
Note The input and output pointers must either be equal or point to non-overlapping buffers. Ref a reference implementation. 注意不能用 yum 的方式安装 libsodium 或 libsodium-devel因为 yum 库收录的版本太低v105ss-libev 并不支持需要按以下方式手动编译安装.
The bug was fixed in Crypto 86. XChaCha20 doesnt require any lookup tables and avoids the possibility of timing attacks. ChaCha20 is a primitive in other words its just one component of a secure cryptographic system and PyCryptodome is a collection of primitives.
Our site uses cookies. The ChaCha20-Poly1305 block may be combined with the AES-GCM multi-booster which implements a high-throughput AES-GCM crypto engine. The purpose of such tokens is to guarantee the integrity of a given message.
Since ChaCha20 is a stream cipher the same operation is used for encrypting and decrypting data. Poly1305 is a MAC and can be used with any encrypted or unencrypted message to generate a keyed authentication token. This combination offers future-proof security as Chacha20-Poly1305 is a mandatory AEAD as is the AES-GCM in TLS 13.
A recent scan from TrustWave is listing this vulnerability. Its original design expands a 256-bit key into 264 randomly accessible streams each containing 264 randomly accessible 64-byte 512 bits blocks. New users should use aeadchacha20 instead.
ChaCha20Poly1305 is an authenticated encryption scheme that combines ChaChaTLS and Poly1305The scheme uses the IETF versions of the ciphers because it is defined in RFC 8439 ChaCha20 and Poly1305 for IETF ProtocolsThe scheme is somewhat unique because it pairs a stream cipher with an authenticator most authenticated encryption modes pair a block cipher. Similar to ref but uses separate temporary variables instead of a temporary array. DES and Tripple DES 3DES block ciphers with a block size of 64 bits have a birthday bound of approximately 4 billion blocks or 2 to the power of 32 hence the name.
ChaCha20 AVX2 implementation had a bug related to carries. ChaCha20 is a 256-bit cipher.

Chacha20 H File Reference Api Documentation Mbed Tls Previously Polarssl

Chacha20 Algorithm Block Diagram Download Scientific Diagram

Java Chacha20 Poly1305 Encryption And Decryption Example
File Chacha20 Diagram Svg Wikimedia Commons

Chacha20 Poly1305 Crypto Engine Ip Core

Google Online Security Blog Speeding Up And Strengthening Https Connections For Chrome On Android
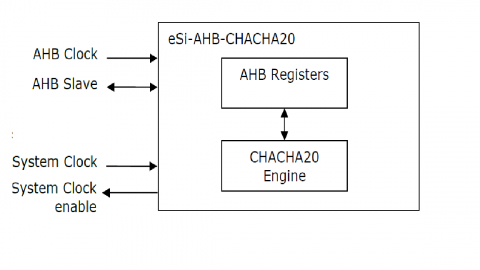
Chacha20 Stream Cipher Core With Ahb Interface

Silex Insight Unveils New Version Of Chacha20 Poly1305 Authenticated Encryption Dsp Valley

4 Authenticated Encryption Real World Cryptography

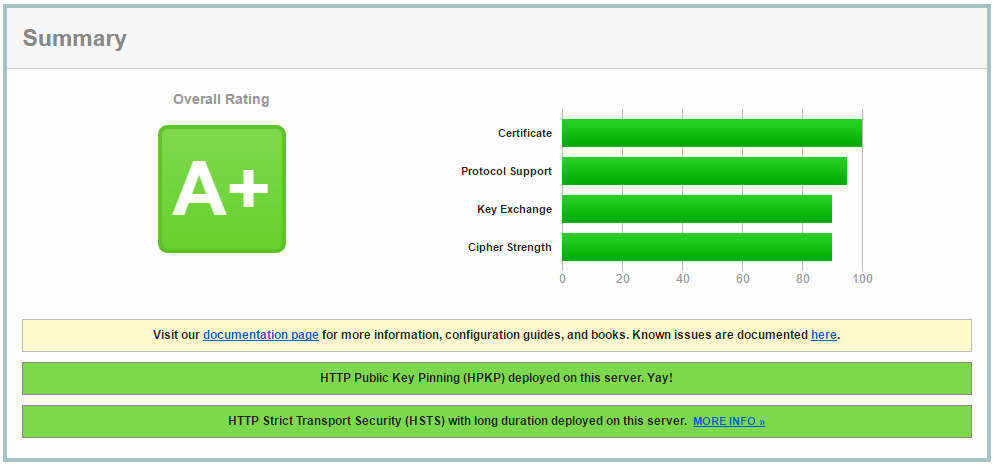
Chacha20 Poly1305 Cipher Summary Adalabs Sparkada Openssh Ciphers

Google Online Security Blog Speeding Up And Strengthening Https Connections For Chrome On Android

Chachapoly H File Reference Api Documentation Mbed Tls Previously Polarssl